Translated by AI to English, originally published on 11 January 2011 in Polish.
2011-01-18 update
I received information that the vulnerability had already been known earlier, in July 2008. The issue was discovered by Józef and described in this forum thread.
2011-01-12 update
On January 12, 2011, Freeconet's management issued an official statement regarding the vulnerability described in this article.
The platform owners reacted immediately—on the day the article was published, the “Add external operator” feature was disabled.
Introduction
Freeconet is a VoIP platform that offers a range of internet telephony services to its users.
At the end of September 2010, I discovered a vulnerability that allows an attacker to intercept calls from Freeconet users to numbers chosen by the attacker.
The attacker has full control over the calls: they can terminate, record, join, and manipulate them in any way.
To demonstrate some of the possible attacks, I created the VOIPROX tool (see below).
Immediately after discovering the vulnerability, I passed detailed information to the platform’s owner.
Unfortunately, despite assurances from Freeconet, the vulnerability was not removed.
That’s why I’ve decided to publish full details about the issue.
I believe in the magic of Full Disclosure—the vulnerability will be eliminated, and Freeconet users will soon be safe.
However, after the fix, the platform’s owner should be urged to investigate whether such abuse has already occurred.
If so, the affected individuals—as well as law enforcement agencies, if necessary—should be notified.
To ensure the credibility of such an investigation, it should be conducted by an external, trusted body, e.g., the Urząd Komunikacji Elektronicznej.
This matter is also important to me personally, as I use this otherwise innovative and probably the most technologically advanced VoIP platform in Poland.
The vulnerability
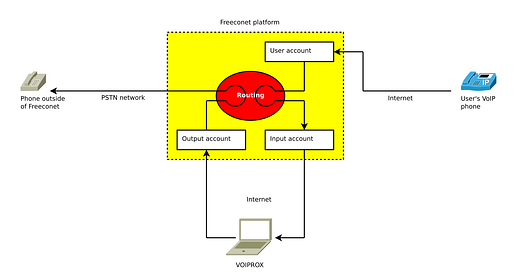
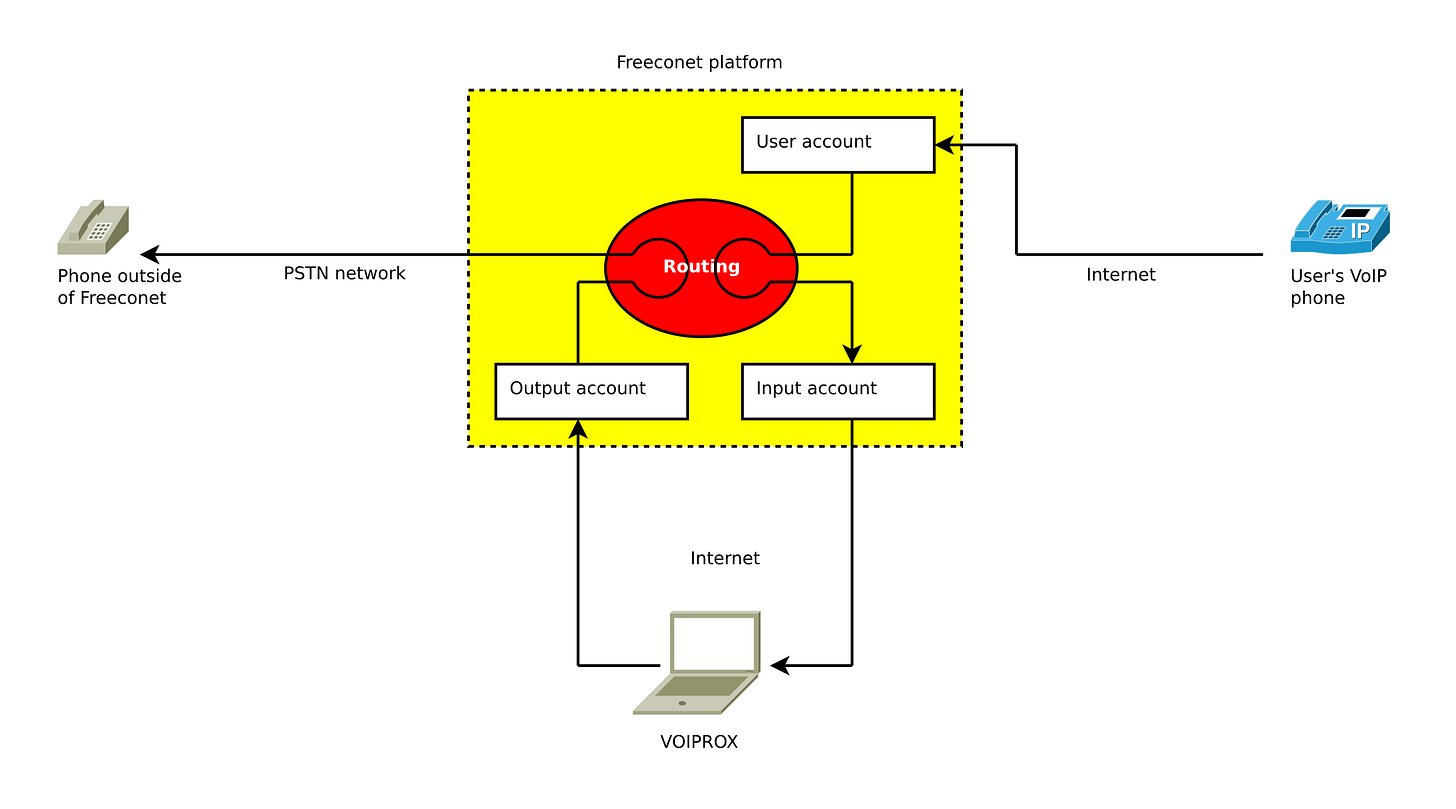
The platform allows you to assign additional phone numbers to a VoIP account—numbers from external, non-Freeconet operators.
The idea is to increase user convenience while reducing call costs.
Let’s assume users A and B are registered on Freeconet.
User A also has a number from a traditional operator and can associate it with their account.
If user B dials that number, the platform sets up an internal network connection, so the call is free.
If the number wasn’t registered, the platform would use traditional telephony, which would result in charges for user B.
Note: It’s user A’s VoIP terminal that rings, not the phone connected to the traditional landline.
This issue is typically solved by using a hybrid gateway or a VoIP phone that can handle both IP and traditional line connections.
That way, a single device handles both types of calls.
The external operator definition feature is available in the Freeconet control panel under Configuration » Operators » External.
Clicking “Add external operator” opens a form where the number and area code are entered in separate fields.
Clicking “Add” links the number to the account—provided the number format is correct and it’s not already linked to another account.
There might be other validation checks, but it’s clear a crucial one is missing: verifying the user’s right to the entered number.
An attacker can enter any number—not owned by them.
From then on, all calls to that number are no longer routed to the actual owner—they go directly to the attacker!
Scope of the threat
Freeconet has between several thousand and several hundred thousand subscribers, depending on the source.
I believe the vulnerability has existed since Freeconet launched in September 2006.
So, for over four years, users have been vulnerable to attacks like those described below.
Attack scenarios
Denial of Service (DoS)
The simplest attack type.
The attacker doesn’t answer calls, hangs up, or simulates a busy line.
This effectively blocks access to the targeted number.
Eavesdropping
As a call is initiated, the attacker starts a parallel call to the same number using traditional telephony (via or outside of Freeconet).
Once the recipient answers, the attacker connects the audio streams of both calls and records them.
The attack is harder to detect if the attacker hides their number or (more difficultly) spoofs the caller’s number.
This way, the callee won’t notice that the call came from a different number.
The attacker can then use fragments of the recorded call to construct misleading or self-serving statements—for example, to carry out the next attack.
Call modification
This builds upon the eavesdropping attack.
The attacker can manipulate the call in real-time—altering pitch, adding echo, or even injecting their own speech.
More advanced versions may target interactive phone systems (IVRs), such as banking lines.
For example, after the victim passes authentication via phone, the attacker disconnects them and continues the call impersonating the user.
How to protect yourself?
Until the vulnerability is fixed, users can protect themselves by changing call routing rules to avoid internal Freeconet calls.
This will increase call costs for calls to other Freeconet users but ensures your calls aren't intercepted.
To do this, go to Configuration » Calling » Routing and set external routing rules for all calls.
VOIPROX tool
To demonstrate the vulnerability, I created a tool called VOIPROX (from VoIP proxy—or, for fun, VoIP rocks!).
The tool logs into two SIP accounts—an input and an output one. It works similarly to a proxy. Incoming calls to the number(s) assigned to the input account (hereafter referred to as intercepted numbers) are received and forwarded to the real recipient via the output account. The incoming call is only answered once the person being called picks up. This prevents a suspicious pause that could alert the caller.
Each intercepted call is automatically saved to a separate WAV file. While the call is ongoing, the user can interact with it in real time via a simple console.
VOIPROX was written in Python. I chose this language because the VoIP library I selected is only available for C and Python.
VOIPROX was written and tested on Linux. However, I see no reason it wouldn't work on other operating systems supported by Python and PJSIP.
To test the tool conveniently, you'll need a separate VoIP terminal, gateway, or softphone (e.g., the web softphone provided by Freeconet). Note: the softphone must run on a different machine than VOIPROX. VOIPROX requires access to a sound card (even if it doesn’t use it) and cannot share it with other software.
Dependencies
Install all dependencies needed to compile PJSIP. You can find detailed instructions here. Pay special attention to the ALSA libraries. If they are not detected, VOIPROX will not support local audio.
Download the PJSIP library (I tested version 1.8.10):
$ wget http://www.pjsip.org/release/1.8.10/pjproject-1.8.10.tar.bz2Unpack the archive and compile the library without installing it:
$ tar jxf pjproject-1.8.10.tar.bz2
$ cd pjproject-1.8.10
$ ./configure
$ make dep
$ makeInstall Python and the necessary packages to compile extensions. You can find all the required information here.
Compile and install the PJSIP extension for Python:
$ cd pjsip-apps/src/python
$ sudo makeCheck installation:
$ python -c 'import pjsua' && echo 'OK'VoIP accounts
You will need three SIP accounts:
Input account: Receives calls to one or more intercepted numbers.
Output account: Used by VOIPROX to make calls to actual recipients.
Test account: Used for testing. If you already have a Freeconet account, you can skip creating this one.
Although in theory, the output account can be registered with any VoIP provider, VOIPROX currently supports only Freeconet accounts. You can create all accounts using the Freeconet registration form.
Assign a phone number, provide your details, email, and login for each account. You can use the same email for all. To distinguish accounts, include the type in the login (e.g., -in, -out, -test).
Account configuration
Log in using the credentials sent to your email and configure:
Output account:
Top up your balance: Payments » Top Up.
Deactivate Freeconet internal calls (see "How to Protect Yourself").
Optionally, hide caller ID: Configuration » Users » Your user » Presentation » Hide.
Input account:
Configuration » Operators » External » Add external operator.
Enter the number to intercept and click Add. For mobile numbers, provide the first three digits (area code) without the leading zero in the first field and the rest in the second.
Note: The number must not be from Freeconet.
Do not use popular numbers (e.g., company hotlines), as intercepting random calls can have legal consequences. Use your own landline or mobile number.
Test account:
If you already have a Freeconet VoIP phone, use it for testing and skip ahead.
Otherwise, after logging in, use the web client under "Call from Website". Try dialing 901 (for free account status info) or Freeconet’s support at 801 009 500.
If calls don’t work, try another SIP client. Configuration info is in the email from Freeconet.
Do not make test calls from the same machine running VOIPROX. Use a separate VoIP device or run a softphone on another computer.
Launching the program
Download VOIPROX:
$ git clone https://github.com/pepawel/voiprox.git
$ cd voiproxStart VOIPROX with SIP credentials:
$ ./voiprox input_login:password1 output_login:password2A short sound confirms correct sound card communication.
If issues occur, run with -v for verbose mode.
First test
Make a call from the test account (on a different device) to the intercepted number set in the input account. The test call is free for the test account but will charge the output account.
After the call, a .wav file will appear in the VOIPROX directory. Congrats—you’ve just intercepted your first phone call. ;-)
Further capabilities
VOIPROX has an interactive console. Type help for commands:
>> help
Possible commands:
list, show - show all active connections
disconnect [[caller|callee] [from]] connection
- disconnect caller or calee from connection given by
connection id; if caller/callee not given entire
connection is terminated
attach [mic|speaker] [to] connection
- attach local microphone or speaker to given connection;
if mic/speaker keyword not given both will be attached
detach [mic|speaker] [from] connection - analogical to attach
play file.wav [to] connection
- play wav file (no spaces allowed in file name)
help - show this help
quit, exit or ^D - terminate all active connections and quitCall and don’t hang up. Use the list command to see active calls:
>> list
1: 123456789 > 0987654321Attach mic/speaker:
>> attach to 1Detach mic to listen only:
>> detach mic from 1Disconnect the caller to impersonate:
>> attach mic to 1
>> disconnect caller from 1Play a WAV file:
>> play test.wav to 1Enjoy—and play nice!
Disclaimer
VOIPROX is a proof-of-concept tool. It may contain bugs. I’ve tested intercepting two calls simultaneously, but not more. Tested on Ubuntu 9.10.
All calls during development were initiated by me and used only for testing.
Use VOIPROX at your own risk. Do not break the law. Freeconet logs all connections—logs may be used as evidence in court.
I hope bad actors won’t use this tool. Public release should pressure Freeconet to patch the flaw quickly, denying criminals time to abuse it. Anyone already secretly exploiting it will lose that opportunity.