Open Source Projects
Active projects
These projects are either under active development or in maintenance mode.
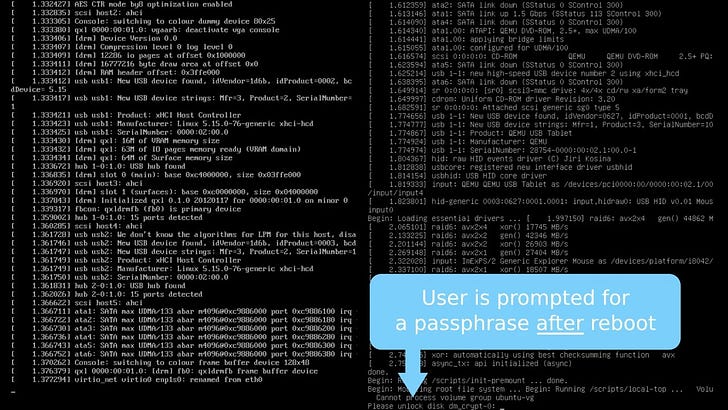
Cryptreboot
A secure and convenient reboot for Linux systems with encrypted root partition. It asks for a passphrase and reboots the system afterward, automatically unlocking the drive on startup using in-memory initramfs patching and kexec.
SXG Status
A Cloudflare worker that allows websites to detect if Signed Exchanges (SXG) subresources were correctly prefetched. Helpful in monitoring prefetching errors, analytics, and performance measurements.
Based on a clever hack combining cloaking with an all-or-nothing SXG principle.
Streching Google Prefetching Demo
Signed Exchanges prefetching demonstration, showing how much data can be prefetched on Google search results. You'll find more information in the post about the demo.
Early projects
These projects were created many years ago, and I don’t maintain them anymore. I've preserved them here as each one demonstrates an innovative concept that was novel at the time of its creation.
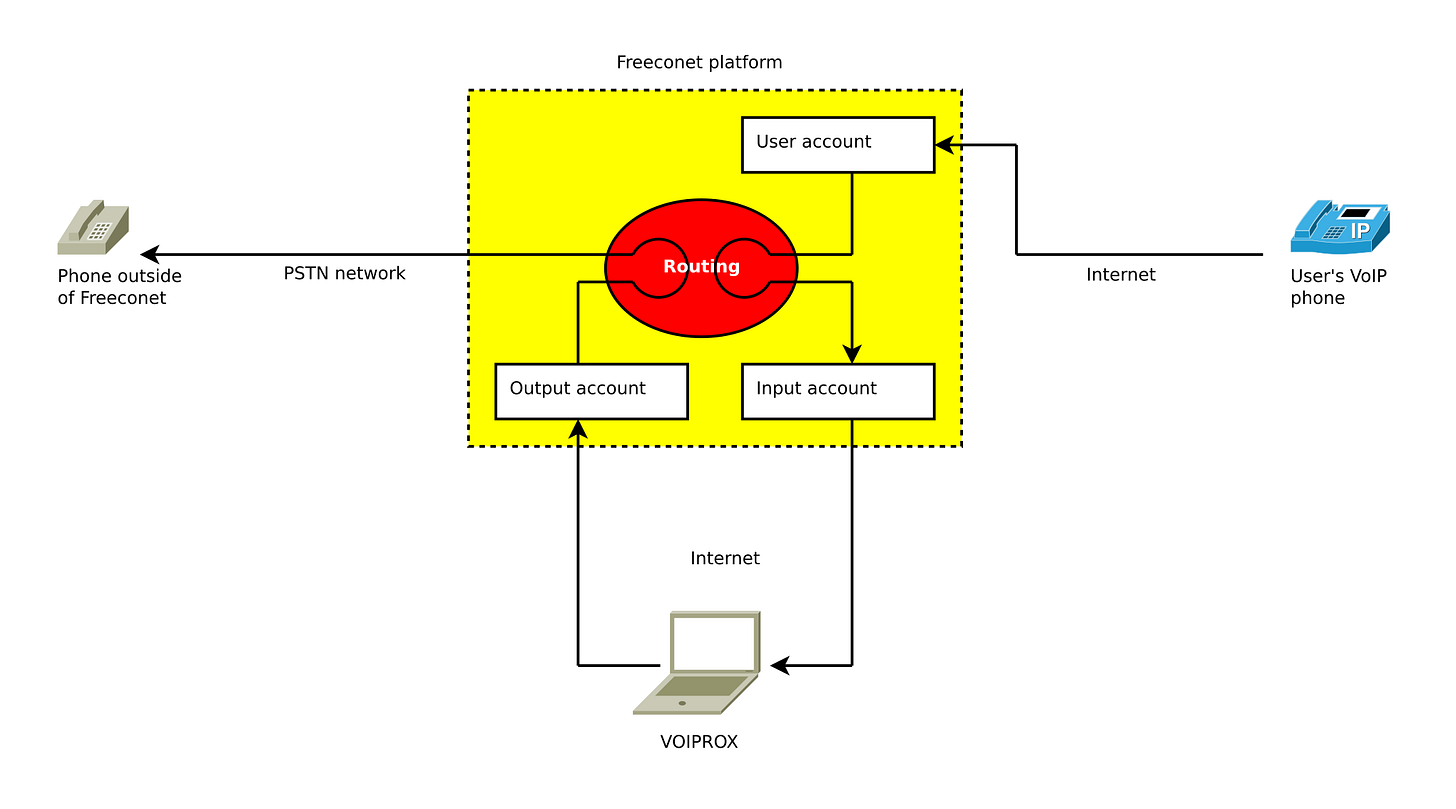
VOIPROX
Demonstration of a man-in-the-middle vulnerability in Freeconet VoIP platform. The tool allowed intercepting calls to any number made by platform users.
The attacker could record and take over the calls by disconnecting one party and impersonating the other. For more details, read the post explaining the vulnerability.
Etherbat
Etherbat performs Ethernet topology discovery between 3 hosts: the machine running Etherbat and two other devices. It uses spoofing to introduce temporary changes in the memory of network switches. Later, it probes them using specially crafted Ethernet frames. The tool could be described as the layer 2 equivalent of traceroute.
# etherbat 10.0.0.1 10.0.0.2
0: 10.0.0.10 (00:12:1b:d8:a9:86)
1: 10.0.0.1 (00:0f:18:ce:5f:29)
2: 10.0.0.2 (00:26:b4:c5:8c:12)
1 2 0
\ / |
*-~-*Example questions answered by Etherbat:
Are the hosts connected to the same switch?
Are they in three separate switches?
Which host is closer to the local machine?
No manageable switches or extra software on remote hosts are required. For more details, see the slides below.
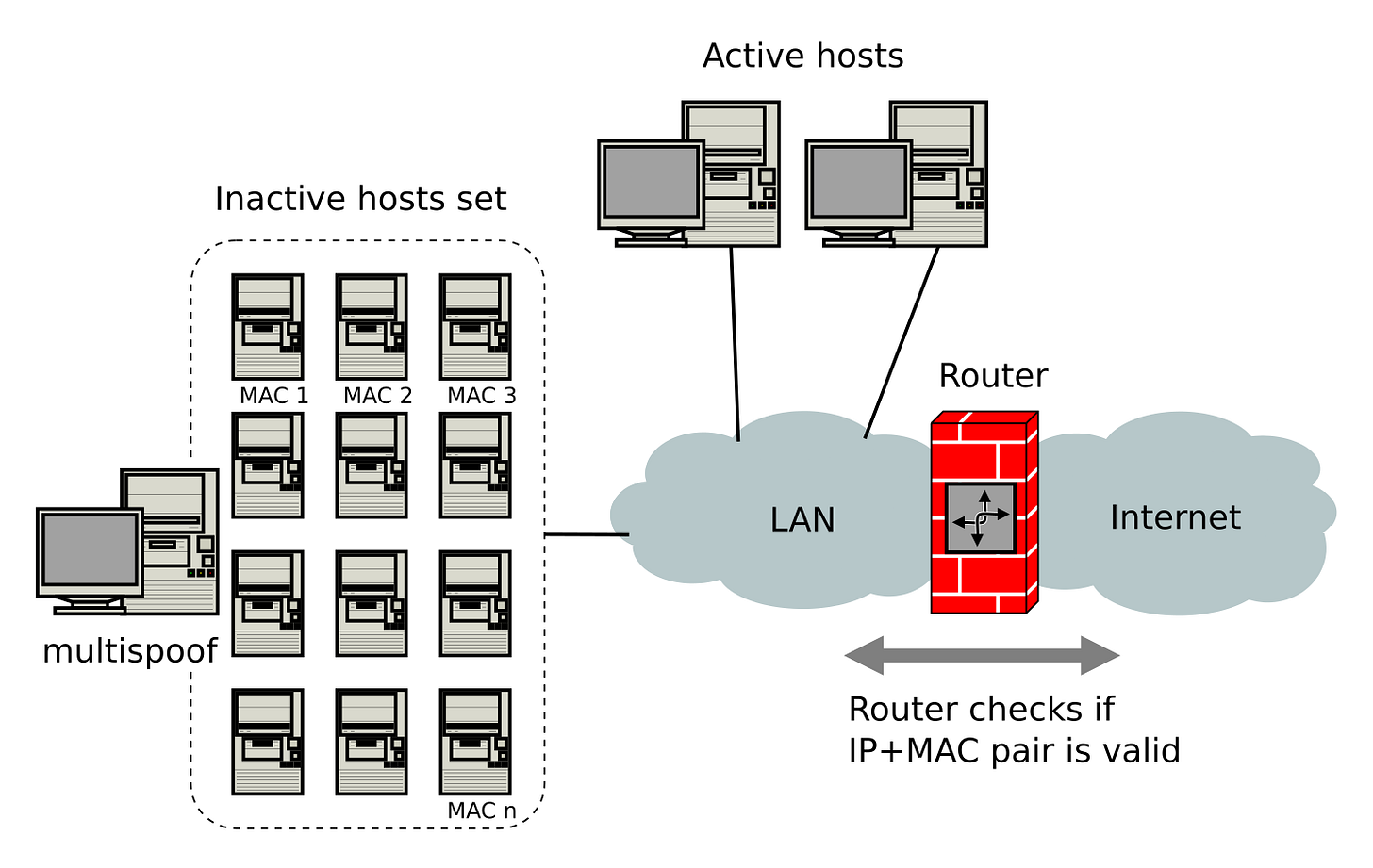
Multispoof
Multispoof is an application that exploits weak, address-based authentication frequently implemented by ISPs in Ethernet networks. In such networks, customers are identified with IP-MAC address pairs, and only those paying ISP are granted access to the Internet.
Multispoof uses IP and MAC spoofing to impersonate legitimate customers. The idea is not new, but multispoof does it smartly. As it impersonates only inactive customers, there are no address conflicts. Using multiple addresses in parallel in combination with load balancing allows to achieve much higher transfer rates.
I've created multispoof as a software project for my M.Sc. thesis under the supervision of Dr. Tomasz Surmacz. You can download my thesis (in Polish) below.
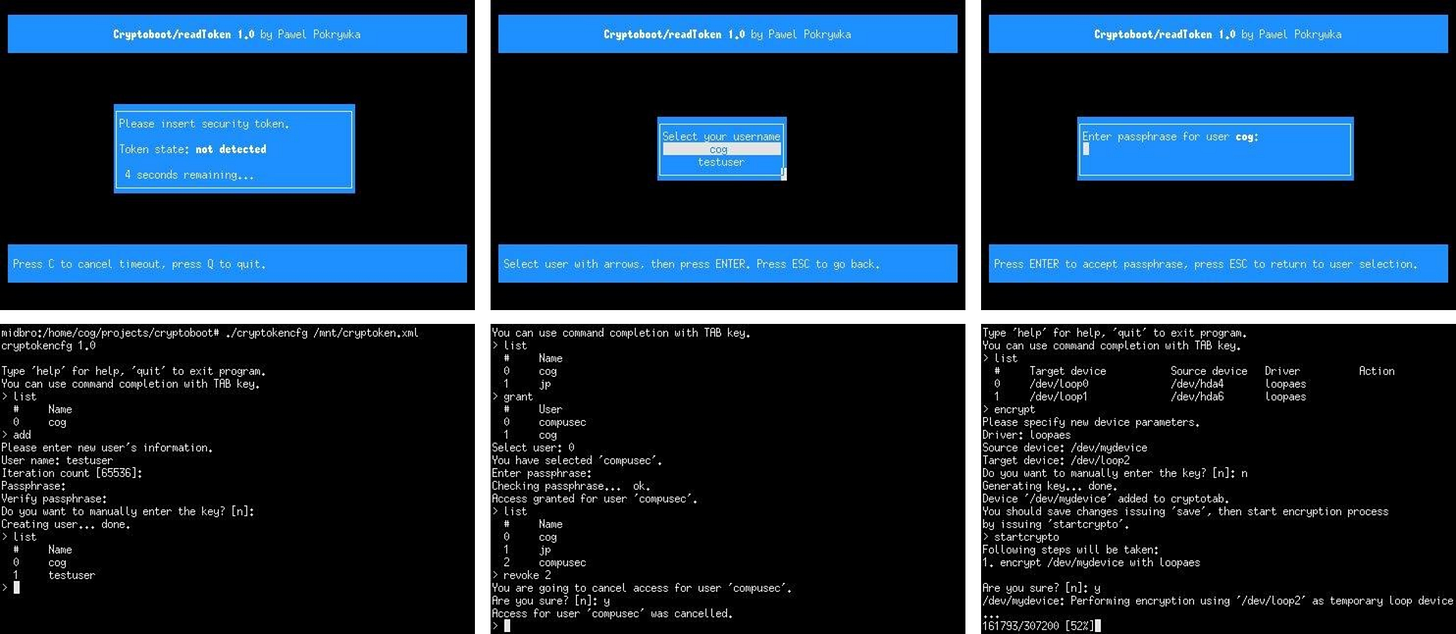
Cryptoboot
An integrated set of tools for disk encryption on Unix. It is especially suited to encrypt root partition using loop-AES. Features include TUI for preboot authentication, multiple users, a CLI admin tool for encryption/decryption of devices, key material storage on an external USB mass-storage device, and PBKDF using PKCS#5.
I started working on this project before the LUKSv1 specification was published by Clemens Fruhwirth and released it roughly at the same time. Since then, the LUKS+dm-crypt duo has taken over the world, and Cryptoboot is no longer relevant.